Packers
Malware is often packed. It produces a smaller version of the executable and more difficult to analyse. A malware analyst will still be able to work with a packed version for a behavioural analysis but for static analysis, an unpacked version may be necessary.
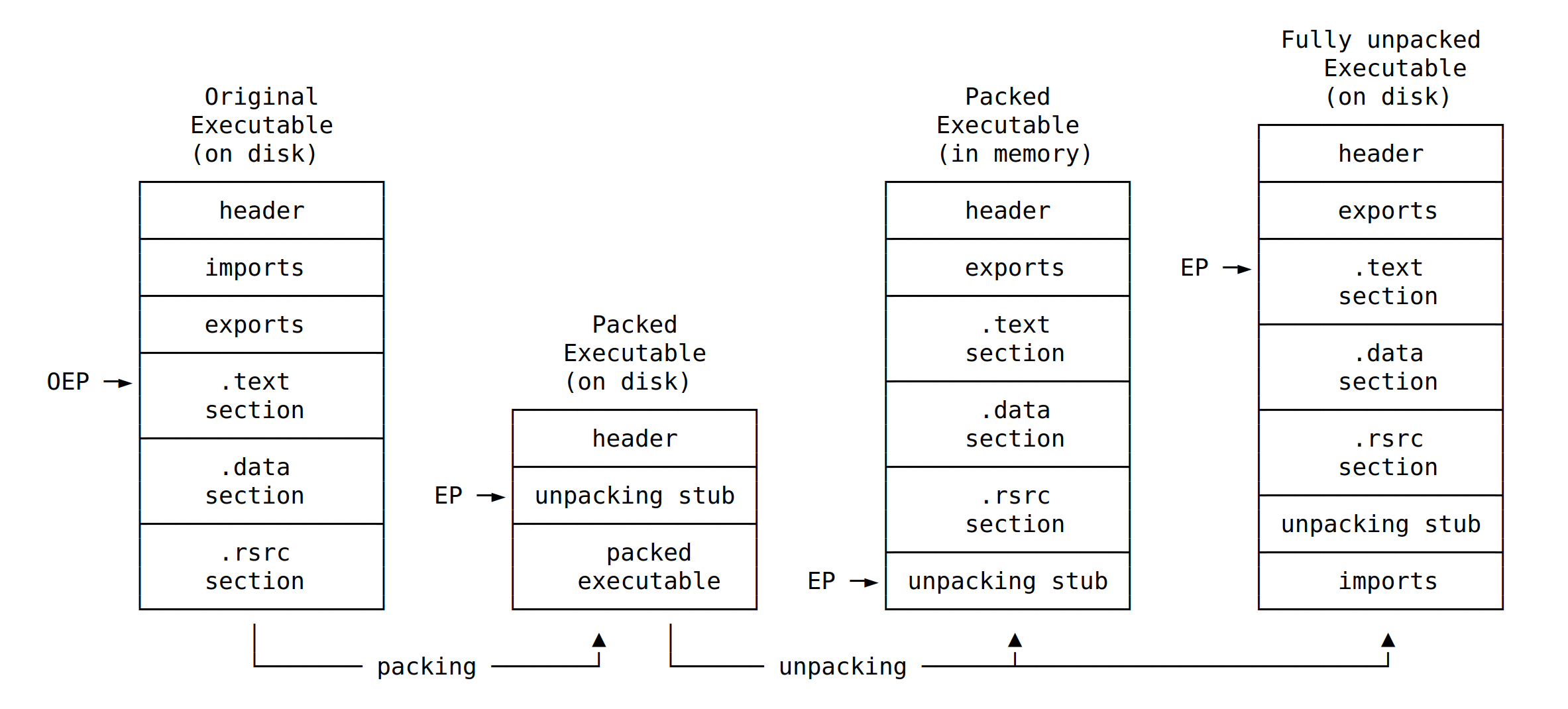 |
|---|
| The unpacking stub unpacks the original executable into memory, resolves imports, and transfers execution to the OEP |
Identifying packers
Opening a packed executable with tools like OllyDbg and IDA-Pro will produce a warning that the executable may be packed.
Packed programs have very few imports (usually
LoadLibraryandGetProcAddress), or no import at all.Many packers leave text signatures inside the packed binary.
In some cases, the
filecommand will be able to identify the packer (UPX compressed,PECompact2 compressed)Tools like PEiD (python version) and pev detect most common packers, cryptors and compilers for PE files.